- by x32x01 ||
This guide covers the essential networking concepts every ethical hacker needs: core protocols, packet analysis, attack/defense techniques, practical commands, and a study plan to get you lab-ready. The goal: understand how networks work so you can find weaknesses and help secure systems - ethically and legally.
Why networking matters for ethical hacking
Networks are the plumbing of modern systems. Vulnerabilities often live in protocol misconfigurations, weak authentication, or unexpected packet behavior. If you can read and reason about traffic - from DNS queries to TCP flags - you can locate misconfigurations, sniff credentials in test labs, and understand how attackers pivot across environments.
Core concepts you must master
Practical tools (must-know)
Quick demo commands you should practice
Ping a host:
Scan common ports with nmap:
Capture 100 packets on interface eth0:
Follow DNS resolution for a domain:
Show listening sockets:
Open and inspect a pcap with tshark (CLI):
Packet analysis essentials (what to look for)
How networking supports attack techniques (and defenses)
Offensive uses (in authorized labs):
Defensive uses:
Common network-layer pitfalls to test for
Safe lab setup & hygiene (how to build practice labs)
30-day networking study plan (practical & hands-on)
Week 1 - Foundations: OSI layers, IP addressing, ping/traceroute, simple Wireshark captures.
Week 2 - Protocol deep dives: TCP (flags, retransmits), UDP behavior, ARP, DNS. Practice tcpdump + Wireshark filters.
Week 3 - Services & scanning: nmap scripts, service fingerprinting, banner grabbing, basic service hardening.
Week 4 - Packet crafting & defense: scapy basics, IDS evasion theory (research-only), and review defensive measures (segmentation, ACLs, TLS).
Daily micro-task: capture a 1-minute pcap, analyze one anomaly, and write a one-paragraph note.
Lab exercises you can do (ethical-only)
Troubleshooting & debugging tips
Defensive checklist for network security teams
Resources & learning links (recommended)
Final thoughts - think in packets, not just ports
Ethical hacking without solid networking knowledge is like exploring a city blindfolded. Learn to read packets, understand flows, and reason about how network components interact. That insight turns noisy scans into actionable findings and helps you recommend fixes that make systems genuinely safer.
Be ethical, document everything, and always test with permission. Happy learning - and enjoy the packet chase!

Why networking matters for ethical hacking 
Networks are the plumbing of modern systems. Vulnerabilities often live in protocol misconfigurations, weak authentication, or unexpected packet behavior. If you can read and reason about traffic - from DNS queries to TCP flags - you can locate misconfigurations, sniff credentials in test labs, and understand how attackers pivot across environments.Core concepts you must master 
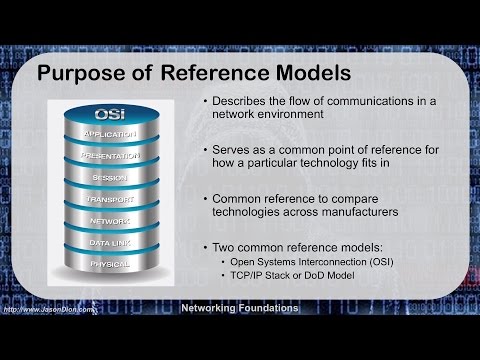
- OSI vs TCP/IP models: Know layers 1-7 (physical → application) and which protocols live where.
- IP addressing & routing: IPv4, IPv6, subnets, CIDR notation, default gateway behavior.
- Ethernet & MAC addresses: ARP, switching, and MAC spoofing fundamentals.
- TCP vs UDP: Connection-oriented vs connectionless, 3-way handshake, sequence/ACK, and common misuse patterns.
- DNS basics: Resolution flow, record types (A, AAAA, CNAME, TXT), and DNS cache poisoning concepts.
- HTTP/S and web basics: Methods, headers, cookies, TLS handshake basics.
- Ports & services: Well-known ports, discovery, and service fingerprinting.
- NAT & firewall behavior: How private→public networks map and what that means for scanning and pivoting.
Practical tools (must-know) 
- Wireshark / tshark - packet capture + analysis.
- tcpdump - CLI packet capture.
- nmap - host discovery & port/service scanning.
- netstat / ss - socket state & listening services.
- traceroute / tcptraceroute - path discovery.
- dig / nslookup - DNS queries and troubleshooting.
- curl / httpie - HTTP testing.
- iptables / nftables - firewall rules demo (defense).
- scapy - custom packet crafting (lab use only).
- mitmproxy / Burp - intercepting HTTP(S) in testing labs.
Quick demo commands you should practice  (safe examples)
(safe examples)
Ping a host: ping -c 4 8.8.8.8Scan common ports with nmap:
nmap -sS -sV -Pn -p 1-65535 target.example.comCapture 100 packets on interface eth0:
sudo tcpdump -i eth0 -c 100 -w capture.pcapFollow DNS resolution for a domain:
dig +noall +answer example.comShow listening sockets:
ss -tulnOpen and inspect a pcap with tshark (CLI):
tshark -r capture.pcap -Y "http.request"Packet analysis essentials (what to look for) 
- Handshakes & flags: SYN/SYN-ACK/ACK sequence, retransmissions, RSTs.
- Unencrypted credentials: Basic auth, HTTP POSTs in test labs - detect them.
- Anomalous TTL or IP IDs: Signs of spoofing or middleboxes.
- DNS anomalies: Unexpected TXT records, suspicious CNAME chains, or data exfil via DNS.
- Large flows & odd ports: Data exfil channels often use uncommon ports or persistent TCP streams.
How networking supports attack techniques (and defenses) 

Offensive uses (in authorized labs):- Port/service discovery → identify outdated services.
- ARP spoofing → simulate MitM in controlled networks.
- DNS spoofing → test resilience of DNSSEC or local resolver configs.
- Packet injection/crafting with Scapy → validate IDS/IPS rules.
Defensive uses:
- Monitor for lateral movement indicators (unusual SMB or RPC traffic).
- Baseline normal traffic patterns to detect anomalies.
- Use strong segmentation and ACLs to limit broadcast domains and attack surface.
- Force encryption (TLS) and HTTP Strict Transport Security (HSTS).
Common network-layer pitfalls to test for 
- Open management ports (RDP, SSH) on internet-facing hosts.
- Misconfigured firewalls allowing internal-only services externally.
- Weak or default SNMP communities exposing device details.
- Split DNS issues where internal names leak externally.
- Unprotected guest networks bridging to internal VLANs.
Safe lab setup & hygiene (how to build practice labs) 
- Use virtual labs (VMware, VirtualBox, or cloud VMs) with isolated networks.
- Create multiple subnets and a simulated router/firewall to practice routing/firewall rules.
- Seed your lab with intentionally vulnerable services (old SSH, outdated web apps) on separate VMs.
- Capture traffic with a dedicated monitoring VM (SPAN/mirror or bridged interface).
- Snapshots are your friend - revert after destructive tests.
30-day networking study plan (practical & hands-on) 
Week 1 - Foundations: OSI layers, IP addressing, ping/traceroute, simple Wireshark captures.Week 2 - Protocol deep dives: TCP (flags, retransmits), UDP behavior, ARP, DNS. Practice tcpdump + Wireshark filters.
Week 3 - Services & scanning: nmap scripts, service fingerprinting, banner grabbing, basic service hardening.
Week 4 - Packet crafting & defense: scapy basics, IDS evasion theory (research-only), and review defensive measures (segmentation, ACLs, TLS).
Daily micro-task: capture a 1-minute pcap, analyze one anomaly, and write a one-paragraph note.
Lab exercises you can do (ethical-only) 
- ARP reconnaissance in an isolated lab: observe ARP tables and MAC changes.
- HTTP analysis: spin up a test web server and inspect request/response headers.
- DNS exfil simulation: locate how data could be encoded in TXT records (lab-only, never against real infra).
- TLS inspection: configure a test server with weak ciphers and observe alerts from modern clients.
Troubleshooting & debugging tips 
- When captures are noisy, use display filters (Wireshark) e.g.,
ip.addr == 10.0.0.5 && tcp. - Correlate timestamps across logs (system logs, capture timestamps, application logs).
- Use
ngreportsharkfor quick string-based filters in large files. - Verify MTU issues with
ping -M do -s SIZEto test fragmentation behavior.
Defensive checklist for network security teams 
- Enforce least privilege routing and ACLs.
- Disable unused services and restrict management interfaces.
- Use strong authentication and rotate keys/certs.
- Encrypt sensitive links with TLS and use up-to-date cipher suites.
- Log and monitor baseline traffic; set alerts for unusual spikes.
- Periodically run authorized internal scans and red-team exercises.
Resources & learning links (recommended) 
- RFC reading list: RFC 791 (IPv4), RFC 793 (TCP), RFC 1035 (DNS).
- Wireshark University & Practical Packet Analysis.
- Try a hands-on course: TryHackMe, Learn Networking on YouTube (start with the provided lecture).
- Practice CTF network challenges and read write-ups.

👆 Click The Image To Watch The Video 👆
Final thoughts - think in packets, not just ports 
Ethical hacking without solid networking knowledge is like exploring a city blindfolded. Learn to read packets, understand flows, and reason about how network components interact. That insight turns noisy scans into actionable findings and helps you recommend fixes that make systems genuinely safer.Be ethical, document everything, and always test with permission. Happy learning - and enjoy the packet chase!
Last edited: